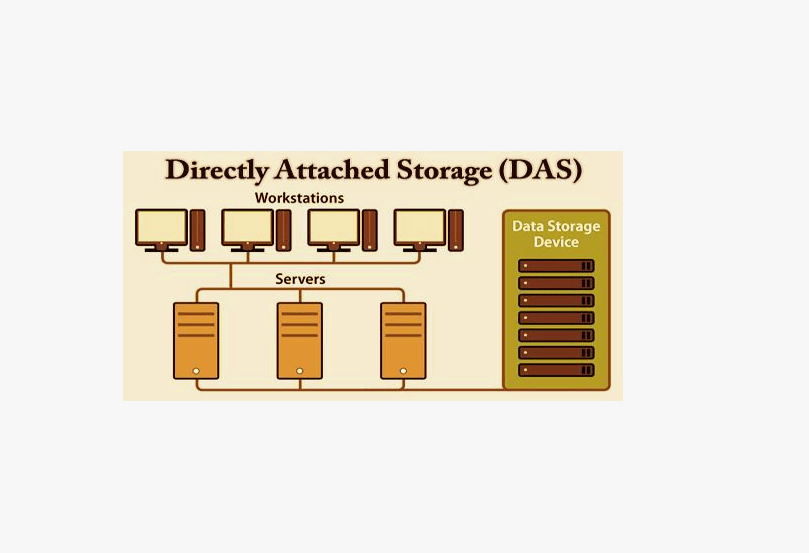
Businesses depend heavily on efficient storage solutions to manage their vast data. One such solution is Direct Attached Storage (DAS).
This storage system directly connects hard or solid-state drives to a computer or server, providing fast and accessible data storage.
While DAS offers significant performance benefits and cost-effectiveness, it also comes with security challenges.
As businesses increasingly rely on DAS for their storage needs, understanding these security risks and how to mitigate them is crucial to protecting valuable data.
Let’s explore the potential security risks of using DAS and the best practices businesses can adopt to ensure their data remains secure:
What Is DAS, And Why Do Businesses Use It?
Before diving into the security risks, it’s essential to understand why DAS is so popular. DAS is often used by small to mid-sized businesses that need reliable storage but cannot afford the complexity and expense of more sophisticated systems like Storage Area Networks (SAN) or Network Attached Storage (NAS).
With DAS, devices are physically connected directly to servers or computers via USB, SATA, or other interfaces. This makes it simple to set up, cost-efficient, and high-performing for applications requiring quick data access.
However, as businesses grow and data management becomes more complex, the security of DAS must be a primary consideration.
While DAS provides numerous benefits, it also introduces certain vulnerabilities that can be exploited by malicious actors if left unprotected.
Lack of Centralized Management and Control
One of the primary security risks of using DAS is the need for centralized management. Unlike NAS or SAN, networked storage solutions allow centralized control, and DAS devices are typically directly connected to a single computer or server. This decentralization can result in the following security issues:
- Inconsistent Data Protection: Since DAS is not centrally managed, it may not be protected by the same security protocols enforced in larger networked systems. This can leave the storage vulnerable to threats other networked systems have already mitigated, such as data encryption, access control, and regular backups.
- Difficulty in Monitoring and Auditing: With a centralized control system, tracking who accesses the data and identifying potential breaches becomes significantly easier. In larger networks, access controls, user permissions, and audit logs provide a clearer picture of who is accessing which data and when. This kind of monitoring may be impossible or inadequate in a DAS setup.
To mitigate this risk, businesses should implement local backup and data encryption strategies. Additionally, software tools that allow for individual monitoring of DAS devices can help track activity and access.
Encryption can protect sensitive data from unauthorized access, and ensuring the devices are regularly backed up prevents data loss in case of a breach or failure.
Data Breach Vulnerabilities
Since DAS typically involves direct physical connections to computers, one of the most pressing security risks is unauthorized physical access to the storage devices. If someone can physically connect to a DAS device, they may be able to bypass the operating system’s security settings and access the stored data.
- Physical Theft: If DAS devices are not secured, they can be stolen. A thief could bypass encryption or access controls by removing the device and connecting it to another system.
- Unauthorized Access: A malicious actor with physical access to the DAS could access sensitive information without network-based barriers, especially if strong authentication methods aren’t in place.
Securing DAS devices is the first line of defense against physical breaches. Businesses should consider physically locking DAS storage devices in secure, access-controlled environments.
Furthermore, encryption should be enabled at the device level to ensure that the data remains unreadable even if the device is stolen without the proper decryption key.
Additionally, enforcing multi-factor authentication (MFA) and strong password protocols for accessing DAS systems can further limit unauthorized access.
Limited Scalability And Redundancy
Another security challenge posed by DAS is its limited scalability and redundancy. As a standalone storage solution, DAS does not inherently offer the same fail-safes and redundancy options as more complex systems like SAN. This can create serious security risks in the event of a hardware failure:
- Data Loss: Without a backup or redundant storage option, if the DAS device fails or is corrupted, the data could be lost permanently, especially if regular backups are not performed.
- Single Point of Failure: In larger systems, redundancy mechanisms such as RAID arrays ensure that data remains available even if one storage device fails. With DAS, the absence of this redundancy means that a failure in the device could lead to significant downtime and potential data loss.
Businesses using DAS should implement regular backup procedures to avoid data loss and minimize downtime. Offsite or cloud backups can provide additional protection in case of a disaster.
Moreover, businesses can configure RAID setups on their DAS devices for redundancy, ensuring that data is mirrored or striped across multiple disks to safeguard against hardware failure.
Conclusion: Securing DAS For The Future
While DAS offers businesses a cost-effective and high-performance storage solution, it also presents several security challenges. These risks—from unauthorized physical access to malware infections—can compromise the integrity and confidentiality of valuable data if not properly managed.
Businesses can safeguard their DAS environments by taking proactive steps to implement encryption, secure physical access, ensure redundancy, and integrate with broader network security measures. With these best practices in place, DAS can continue to serve as a reliable and secure storage option for businesses looking to manage their data efficiently in an increasingly digital world.
Ultimately, securing DAS requires a combination of physical security, software solutions, and strategic planning. With the right approach, businesses can enjoy the benefits of DAS while mitigating the potential risks that come with its use.
Read More: Cloud Computing’s Future: What to Expect in the Next 5 Years